There are lots of virtual private networks (VPNs) available for iPhone, iPad, and Mac, and one of them is VPN Unlimited, made by KeepSolid. It is a well-known VPN app that has been around of a long time. Since VPN Unlimited is nearing its 10th birthday, let’s take a closer look at what this tool provides for its users.
Server Network Overview
VPN Unlimited offers a network of over 3,000 servers located in over 80 locations, providing users with a variety of connection options.
Protocols Offered
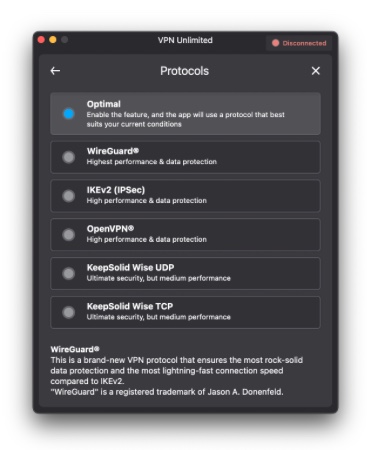
VPN Unlimited provides a selection of VPN protocols. The list includes familiar names such as OpenVPN and L2TP/IPSec, newer entries like Wireguard, and KeepSolid’s proprietary protocol, KeepSolid Wise.
By default, VPN Unlimited selects the most suitable VPN protocol for your connection. However, you have the option to adjust the settings and choose a different protocol if desired. Choosing the best VPN protocol depends on your specific needs and priorities. If security is your top concern, you might opt for OpenVPN, which is widely recognized for its strong encryption and high reliability.
For those seeking speed, especially on mobile devices, WireGuard is a newer protocol that offers fast connections without compromising security. L2TP/IPSec can be a good choice if you’re looking for a balance between speed and security, but it may not be as fast as other options. IKEv2 is particularly well-suited for mobile devices, as it quickly re-establishes a connection if your device temporarily loses its internet connection.
Lastly, some regions with strict internet censorship might require stealthier protocols like KeepSolid Wise or others that disguise VPN traffic. Always ensure your chosen protocol is supported by your device and the VPN service you’re using.
Logging Policy
VPN Unlimited outlines a zero-log policy, asserting that it doesn’t retain any logs of user activities.
A VPN’s zero-log policy is essential for user privacy and trust. Without logging, there’s no record of user activities, ensuring genuine online anonymity. This means even if governments or hackers seek data, there’s nothing to hand over.
Additionally, no logs mean reduced hacking targets, further safeguarding user data. In essence, a zero-log policy reinforces a VPN’s core promise of privacy and should be a top consideration when choosing a service.
Encryption
- 256-bit AES encryption protocol: VPN Unlimited uses this widely recognized standard for data security, offering a high level of protection against potential breaches. It utilizes a 256-bit key length, making it extremely resilient to brute-force attacks and is commonly used by governments and industries to safeguard sensitive information.
- RSA Authenticator: Unlike other systems that might depend on networks, routers, DNS servers, or client devices, RSA’s effectiveness hinges solely on access to the private key. With RSA’s asymmetric nature, messages can be encoded using a public key without revealing details about the corresponding private key used for decoding. This means the public key can be shared online, allowing anyone to send encrypted messages to its holder, yet only the holder with the private key can decipher them.
Split Tunneling
A feature available on Android that allows selective app usage with the VPN. It helps to optimize bandwidth and grants flexibility between local and secure connections.
Kill Switch
The kill switch is important because it ensures that if your VPN connection drops unexpectedly, your internet access is immediately cut off, preventing any data from being transmitted over an unsecured connection and potentially exposing your true IP address or sensitive information.
Blogger Mode
This feature is tailored for bloggers, journalists, and content creators to enhance their online privacy. It allows users to hide their real IP address in the application interface, ensuring that it doesn’t appear in screenshots or screencasts. It’s especially valuable for streamers who might inadvertently show their desktop, preventing potential IP leaks.
By using Blogger Mode, individuals can ensure their IP address remains hidden, protecting them from IP tracking, DDoS attacks, and potential threats on public WiFi networks.
Here are some other VPN Unlimited features that aim to enhance user experience:
- Trusted Networks: By designating certain networks as “trusted,” such as your home or workplace Wi-Fi, VPN Unlimited can automatically disable its connection when you’re on those networks. This automation removes the hassle of manually turning off the VPN every time you access a network you deem safe.
- DNS leak protection: It prevents your real IP address and online activities from being exposed, even if there are vulnerabilities or issues in your VPN connection, ensuring consistent anonymity and security
- Ping test function: measures the time it takes for a small amount of data to travel from your device to a server and back, helping assess the responsiveness and stability of a connection.
Conclusion
VPN Unlimited presents itself as a robust tool in the crowded VPN market, distinguishing its offerings with a mix of classic and proprietary protocols, a firm commitment to user privacy through a no-logging policy, and a suite of features tailored to varied user needs. Whether you’re prioritizing security, seeking optimal speed, or are a content creator needing added layers of privacy, VPN Unlimited’s decade-long legacy, coupled with its versatile functionalities, makes it a noteworthy contender for those exploring VPN solutions.
You can download the VPN Unlimited app on your iPhone, iPad, and Mac from the App Store here.