Apple will introduce new technology allowing the company to detect child sexual abuse material and report it to law enforcement agencies. The company has declared that the unique feature of child sexual abuse material (CSAM) detection protects children from any online harm.
It will include filters blocking sexually explicit photos that are sent and received through iMessage accounts. There’s another feature that’ll block any user from searching CSAM-related terms on Siri and Search.
User files are already scanned by cloud services like Dropbox, Google, and Microsoft for any content violating their terms of service or for content that may be illegal, like CSAM. Apple, on the other hand, hasn’t agreed to scan files in the cloud as it gives its users the option of encrypting their data before they reach the iCloud servers.
The NeuralHash Technology
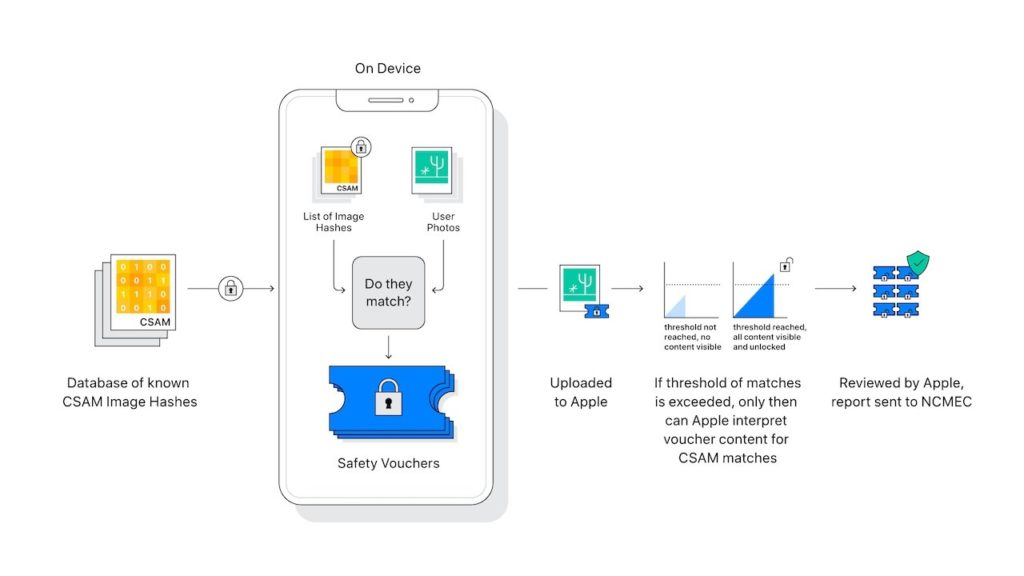
Apple has said that NeuralHash, its CSAM detection technology, can identify any upload of child abuse material to iCloud by working on the user’s device itself. The material isn’t decrypted until they reach a threshold triggering a sequence of checks to verify the materials before they are cleared.
Privacy advocates and security experts have expressed some concerns, as have users aware of how Apple approaches security and privacy, which most other companies lack. Attempting to calm fears, Apple has said that there will be multiple layers of encryption, creating several barriers that need to be crossed before the final manual review of the material.
NerualHash will be introduced in iOS 15 and macOS Monterey. The technology converts photos on any user’s iPhone or Mac into letters and numbers, forming a unique string called a hash. NeuralHash makes attempts to ensure identical and visually similar images create the same hash. If an image is modified, the hash changes, which prevents matching.
Before uploading into iCloud photos, the hashes on a device are matched against a database containing known child abuse imagery hashes provided by child protection organizations like National Center for Missing & Exploited Children (NCMEC). NeuralHash then uses a private set intersection technique, a cryptographic technology, to detect if the hashes match without alerting the user or the image is revealed.
The Public Reaction
Despite the anticipated wide support, users and advocates of privacy remain skeptical as the technology involves an element of surveillance that makes users feel uncomfortable when handed over to an algorithm. There are also demands for more public debates before Apple makes the technology available to users. The Verge reports that some experts fear that the new system will create another surveillance system. Additionally, the concerns include the potential for establishing a way for cracking secure end-to-end encryption.
Having discussed how Apple seeks to check the proliferation of CSAM, let’s now look into how you can gain from Apple’s new iPhone privacy features.
New iPhone Privacy Features: How You Can Take Advantage
At the very core is the question of whether you want to allow any smartphone app to track what digital activity you’re engaged in on other apps and websites. It is a question most apps haven’t taken the trouble to answer, and Apple seeks to change that.
iPhone software will now ask users if they want other apps to track their digital activity in the form of simple pop-ups triggering shockwaves in the ad business, especially at Facebook and Google.
What You Should Do
You’ll first have to ensure that the software on your iPhone is updated to iOS 14.5. To do this, go to the “Settings” app and then tap “General” and finally “Software Update.” It now gives two options: the first is that of pop-ups asking you if you want a certain app on your iPhone to track you.
If you deny permission, your iPhone will make sure that the app receives no tracking details of yours. The second option allows you to turn it off for all apps at one go. Yet again, go to the “Settings” app, but this time you’ll have to tap on “Privacy” and then “Tracking” and then toggle to off the “Allow Apps to Request to Track” option. It means that now apps are barred from asking you if they can track your activity.
Defense Against Tracking
There are certain tips that can help you defend against tracking you do not consent to.
- Use private browsers. Many modern browsers give you adequate protection against techniques like device fingerprinting. Thus, take these elements into consideration when choosing which browser to use.
- Disable third-party cookies. Websites and their partners get to know a lot about you. You can limit their knowledge by refusing the third-party cookies they offer.
- Check app permissions. Some apps tend to get too many privileges on your device. For instance, why would a calculator app need access to your camera or contact list? There is no reason for that. Hence, ensure that all permissions you give make sense.
- Get a VPN. In this age of increased intrusion into user privacy, there is a need to obfuscate your traffic. A VPN encrypts the connection between your device and the internet and hides your IP address. It ensures that your surfing history remains private and that it’s impossible to track you online.
Apple’s efforts to stop the spread of CSAM are commendable. However, privacy concerns remain. While some express these potential issues, others applaud Apple for taking charge.