It seems like there is a new activation lock vulnerability that can give anyone without even having much technical knowledge access to a lost iOS device. This includes the devices that have been marked as lost through Apple’s Find My iPhone service. The technique to gain access to the target iOS device involves a ‘blunt-force’ method that can allow a thief or hacker to get past the Activation lock.
This vulnerability is not new and was supposedly ‘fixed’ by Apple in iOS 10.1.1 after company was informed that iOS 10.1 is susceptible to it. However it has been discovered by Vulnerability Lab that the exploit albeit its variation still works on iOS 10.1.1. How the exploit works is pretty interesting. Since the owner of a lost device can remotely put his or her device in ‘Lost’ mode, when a device is placed in this mode the device asks for Apple ID details of the owner before it can be unlocked. For that to work the person in possession of the device (this can be the owner or the thief) has the ability to connect to a WiFi network.
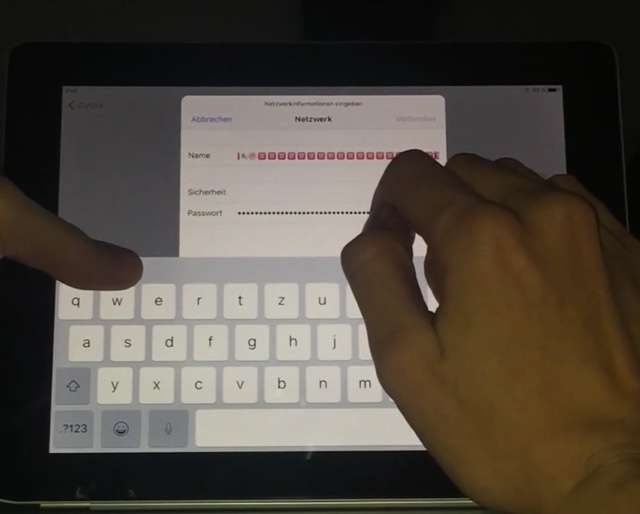
Once the attacker is on the WiFi screen he can select the ‘Other network’ option and then manually enter the network name and password. The attacker can then start copy and pasting a large string of text in both the fields, once enough characters are added (the number can be as big as 10,000 or more characters) the device becomes slow and then completely freezes. When this happens the attacker can put it to sleep using a cover and then remove the cover to gain access to the homescreen.
Apple made some changes in an attempt to block this exploit after iOS 10.1. However the company didn’t do a very good job and in iOS 10.1.1 hackers can still use this exploit but now it requires them to rotate the device and use the Night Shift feature.
From the looks of it the fix to this exploit is a fairly simple one, Apple just needs to limit the number of characters that can be entered in the network name and password fields. However until that fix arrives attackers will have a field day. (Source)