AirDrop is a handy feature that makes it super easy for Apple users to share various types of data with others. While AirDrop adds convenience to our lives, a recent discovery points towards how it also makes us vulnerable to snoops by revealing an iPhone’s phone number. On the Mac the same vulnerability leaks the computer’s MAC address.
The phone number and MAC address sharing vulnerability is not limited to AirDrop only, as iOS’s Wi-Fi password sharing feature also broadcasts the cryptographic hash, which hackers can convert to an iPhone’s phone number. In the case of Wi-Fi sharing feature, the iPhone broadcasts phone number, email address and Apple ID of the user in SHA256 hash. While many users won’t care about their phone number getting revealed to people around them as most of them would already know it, the area this vulnerability raises concern is in public places, where a stranger can find out your phone number and then potentially use it to extract more information about you from the web. Companies can also use this information to track your movements in various retail stores.
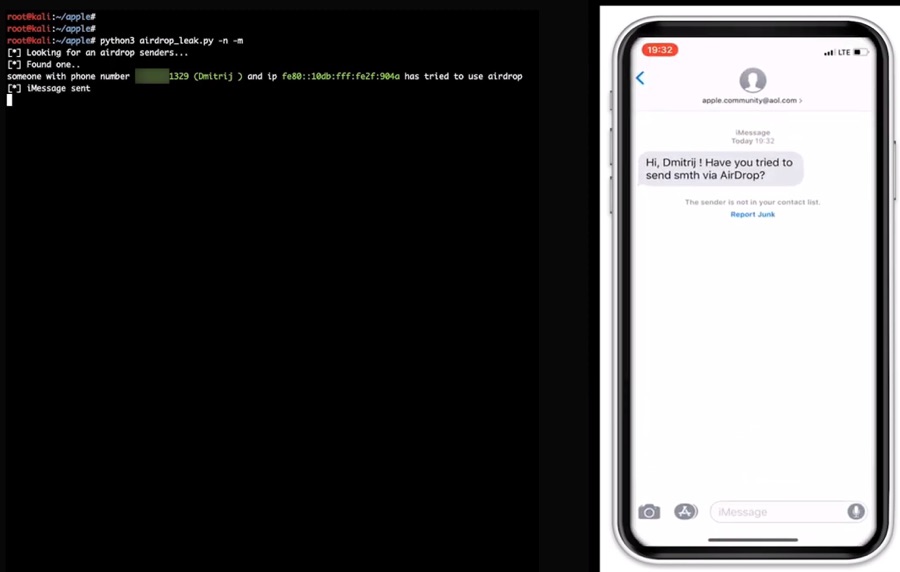
When AirDrop feature is turned on an iPhone broadcasts first three bytes of a SHA256 hash with user’s phone number. It does so to verify the other device belongs to a contact of the user or is someone the iPhone’s owner trusts. However researchers at security firm Hexway say that these three bytes provide enough information that can be used to extract the full phone number.
Security firm Hexway, which has published a report on this vulnerability has also created a proof-of-concept software, which is capable of extracting phone numbers and other information from nearby iPhones and Apple Watches. The software needs to be running a laptop with wireless packet sniffer dongle.
There’s not much Apple can do to prevent it
Errata Security CEO Rob Graham says that there’s not much Apple can do to prevent this from happening going forward, as iPhone needs to broadcast part of the phone number in the SHA256 hash to make sure it is connecting and sharing AirDrop data to a trusted device.
Apple has tried to make it harder to discover the user’s phone number by sharing it in a SHA256 hash, but that is the extent to which the company can go while also offering convenience features like AirDrop.