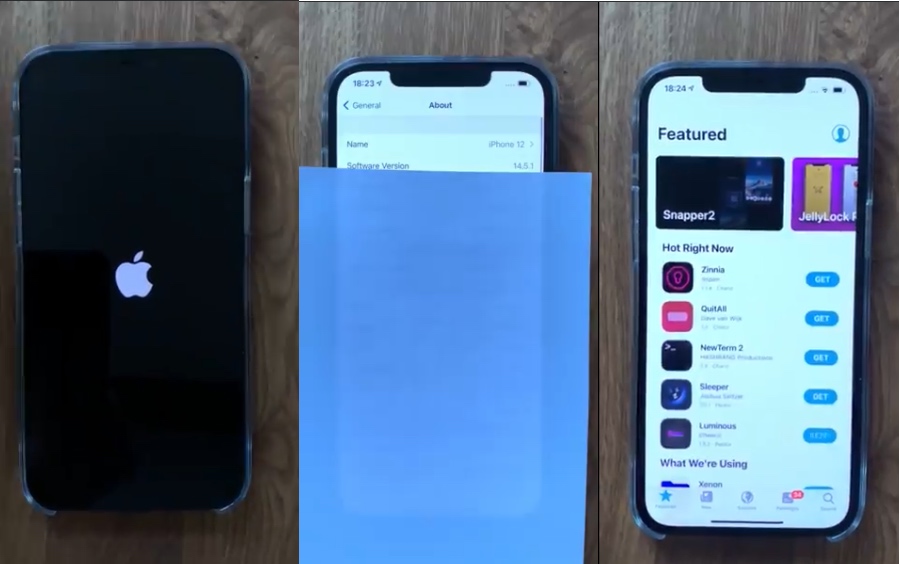
It has been years since we saw an untethered jailbreak getting a public release. Now Linus Henze has posted a video on Twitter that shows his iPhone 12 Pro Max running iOS 14.5.1 having an untethered jailbreak.
Most jailbreaks that we have seen in the recent past were semi-untethered meaning they required the user to re-jailbreak through an app in order to activate the jailbreak. This include the unc0ver and Taurine jailbreaks.
Untethered jailbreak is different from semi-untethered jailbreak because it does not require a re-jailbreak after the device reboots. The jailbroken state of the device remains intact after a reboot, allowing users to enjoy jailbroken state of their iOS device without interruption.
In the video we can see that Henze boots up his iPhone 12 Pro Max and then proceeds to launch Sileo, which runs without any hiccups. If this was a semi-untethered jailbreak, he would have to run some kind of jailbreaking app before Sileo could be used on the device along with other jailbreak related stuff.
Hacker Linus Henze has listed the exploits CVE-2021-30740, CVE-2021-30768, CVE-2021-30769, CVE-2021-30770, and CVE-2021-30773, which he says were used in this demo.
All of these exploits were patched in iOS 14.6 and iOS 14.7 releases, meaning those running iOS 14.5.1 or lower should be able to take advantage of this untethered jailbreak based on these exploits if it was ever released for public.
While we cannot know for sure until a release has been made for the exploits, Henze has a history of releasing exploits in the past.
If these exploits that can be used to create an untethered jailbreak are released to public, it will then be on jailbreak teams of unc0ver and Taurine to implement them on their tools.