If you follow tech news, then chances are you are already familiar with the Safari bug that was leaking browsing history and Google ID to hackers. Hackers could use an exploit found in IndexedDB to access URLs of recently visited websites as well as user’s Google ID.
The Safari bug was found in iOS 15.2.1, iPadOS 15.2.1 as well as macOS Monterey 12.1. Apple acknowledged the bug and started working on fixing it as soon as it was revealed. Now it is being reported that Apple has already fixed the Safari bug in its recently seeded Release Candidates for iOS 15.3, iPadOS 15.3 and macOS Monterey 12.2.
All three of the Release Candidates are currently available to developers for testing, and if everything goes according to plan they will be released to public in the next few days.
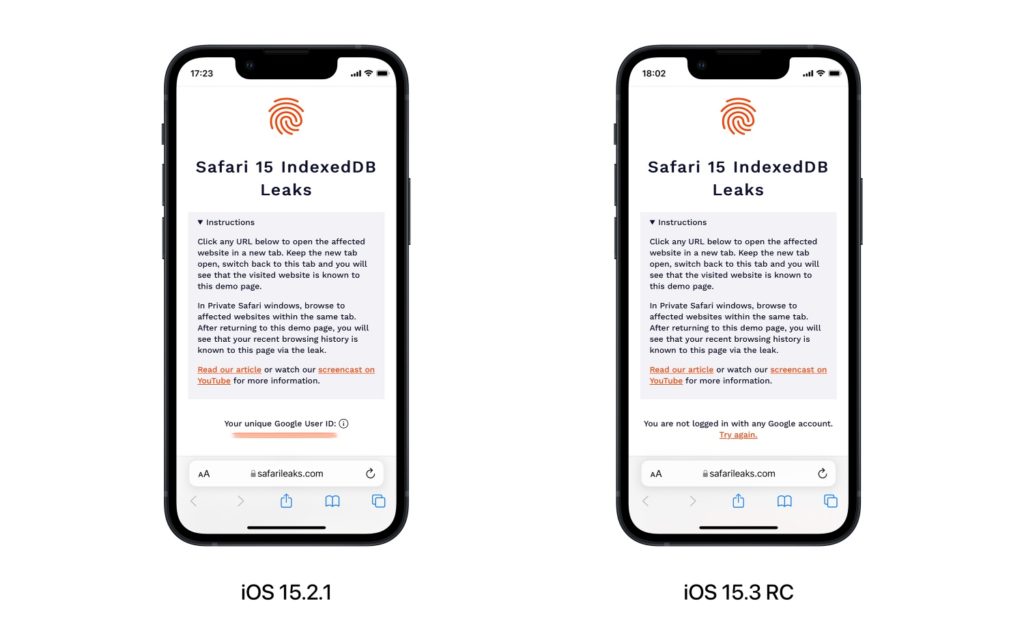
Currently if you are running iOS 15.3 on your iPhone you can head over to FingerprintJS’s demo website that shows the bug in action and see the bug is no longer there.
On a device that is running iOS 15.2.1 or lower the demo website will be able to read Google User ID, whereas on iOS 15.3 Release Candidate it is unable to do so. This indicates that the bug is no longer there and has been fixed in the new update.
Similar results were seen when opening the demo website on macOS Monterey 12.1 vs macOS Monterey 12.2 RC since the bug was not found in the later release.
While we wait for Apple to release iOS 15.3 and macOS Monterey 12.2 to public it is recommended that you do not use Safari browser on your iPhone, iPad or Mac and instead rely on a third-party web browser like Chrome in the meantime. (9to5Mac)