iOS and OS X have long been counted among the safest operating systems, as they have been target to a lower number of viruses and malwares than competing OSs. While non-jailbroken iOS is still very secure thanks to Apple’s walled garden, hackers have been trying ways to penetrate into millions of iOS devices out there, and it seems like they have found a way. A new malware that is being dubbed as XcodeGhost has emerged from China, which uses the OS X compiler to get into iOS apps. The malware stores its malicious code into the Mach-O object file that was packaged into the Xcode installers. The hackers uploaded these installers to Chinese cloud service run by Baidu, so that legitimate developers would download them, while being unaware of the fact that they have been infected with malicious code.
The cleverly made XcodeGhost malware directly infects the legitimate apps being developed for iOS devices instead of affecting the devices themselves. These apps once created enter the App Store and then onto user’s devices, where they start taking user’s private data and upload them to a remote server.
Since only Chinese developers have been using the infected Xcode installers the hack is only found on China based apps, however since some 76 popular apps that includes WeChat messenger andNetEase Cloud Music App have been affect, it is suspected that a large number of devices would have become target of this malware.
The primary reason these developers got compromised versions of Xcode is because they got their copies from third-party sources instead of downloading the Xcode tool from the Mac App Store. The reason for this can be because of the large size of the Xcode software, developers try to avoid downloading it and instead tend to get it from other sources, such as from a friend or a faster unofficial website that hosts such softwares.
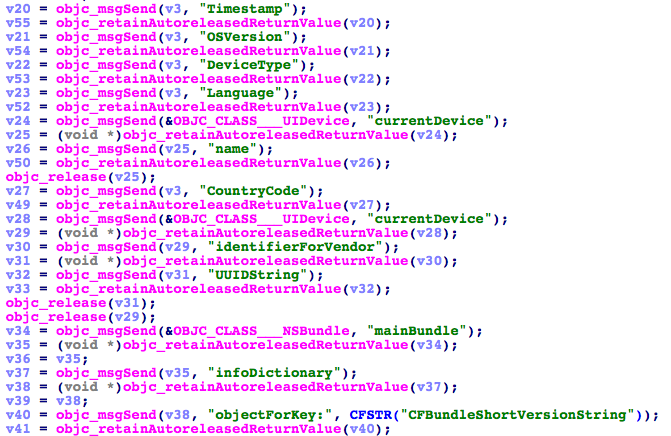
The malware comes into action when an infected app is starts running on an iOS device or is ran in an iOS Simulator. Once its active the malware collects time, app’s name, its bundle identifier, current device’s name and type, its system language and country, its UUI and Network type. After collecting this data it transfers the information to a remote server run by the hackers.
What makes XcodeGhost particularly dangerous is that it does not even require devices to be jailbroken to affect them. The malware has also made its way into the App Store hiding into legitimate applications, that were approved by Apple. If this hack is widely utilized into more apps that target the worldwide audience or have enterprise clients then results can be catastrophic.
Popular jailbreak team Pangu have released a tool that allows users to check if their device is affected by XcodeGhost malware. You can follow this guide to find out if your device is affected or not.
[PaloAltoNetworks]