Nowadays more and more users are using their iPhones and iPads to make online payments. Thanks to the ongoing pandemic users have grown more accustomed to buying products online and make online payments right from their iOS device.
While its is easy to make online payments on iPhone users need to be wary of consequences if they end up getting hacked or their payment details get stolen.
While iOS devices are generally safer than Android when it comes to malware, Apple users still need to take care when making online payments with their mobile device.
There are multiple ways you can make your online payments safer on iOS. By following these tips you can avoid getting scammed and losing your payment information to hackers and scammers.
Use Apple Pay
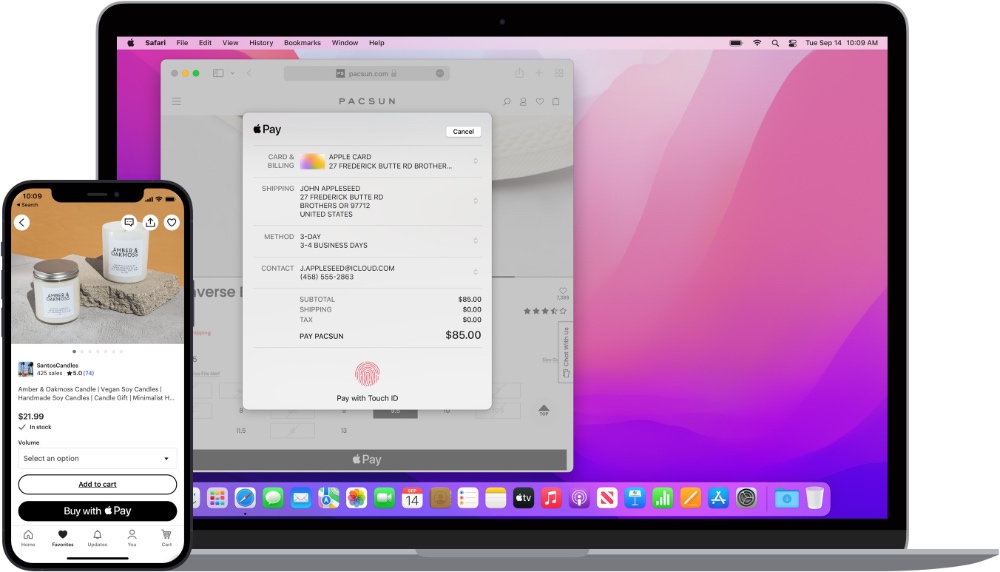
Many users don’t know this but you can make online payments in Safari via Apple Pay. When you pay with Apple Pay on a site that supports it your credit card information is not shared with the website.
This way you significantly reduce your risk of getting scammed or your payment information getting leaked by the website you are making the payment to.
When making payments look for the ‘Buy with Apple Pay’ button and use it as your payment option.
Secure your network
One of the most important steps you can take in order to make your online payments safer on iOS is by using a secure network. The first thing you should do when buying something online is to avoid public Wi-Fi networks. Instead of a public Wi-Fi try using your cellular internet or make payments only when connected to a trusted Wi-Fi network at home.
You can also rely on a good VPN network in order to secure your account. A good VPN provides strong encryption, security protocols and leak protection to protect your payment information. There are plenty of reliable VPN services that you can use. I have personally used NordVPN and Cyberghost VPN apps on my iPhone and iPad. You can click here to read the Cyberghost VPN Review.
Use Credit Card For Payments
If your payment information gets leaked then you are better off if it is a credit card than a debit card. This is because credit cards offer better fraud protections than a debit card.
Most credit cards offer zero-fraud liability policies and reimburse you for any unauthorized or fraud charges made to your card. This is contrary to debit cards where users are not offered such privileges and users are liable for any fraud charges made into their accounts.
Monitor Your Account Statements
If you shop online often, then it is a good idea to monitor your credit card statements for any unauthorized charges. Keeping an eye on your credit card transactions and looking for unknown transactions no matter how small they are can indicate that your card information is being misused.
If you find any anomalies in your account statements, then block your card immediately by contacting the issuing bank.
Pay at trusted sites only.
When you are making a payment on a website you should make sure whether you can trust that website or not. A good way of doing this is to shop only from businesses that you trust in real life. Is the website you are paying at is a trusted retailer with good reviews and has real world presence? By making sure of this you can not only save yourself from trouble of getting hacked but also receive a product that is worth paying for.
One way of checking if a website is trustworthy is looking at the “https://” prefix in its URL. In addition to that you should look for a lock symbol in the address bar. While this does not guarantee the website is not scam, it can protect you from phishing attacks by making sure website owner is using encryption to transfer data in order to protect from hackers.