Your Mac, be it an iMac or MacBook, is shiny and powerful and everyone wants to have it, even hackers and data thieves. For Mac users, the device holds their world, including files, photos, videos, music, and other important stuff.
Data theft and cyber-attacks have crippled many businesses and organizations. The only reason for such insecurity is the lack of protection. If you have not implanted a strong quality assurance program or policy, it’s time to think of a better way to protect vital information.
Weak passwords, poor practices of information management, and unattended computers are some of the few reasons that make your Mac vulnerable to hackers and criminals. Hackers find the weakest targets to tunnel into your business from loose sources such as mobile phones or tablets.
With the help of smart encryption software, it is possible to remediate such vulnerability and threat, thus making it tough for rookie hackers and competitors to penetrate the device. However, only the software cannot prevent hacking. Mac users have the resources and authority to protect it from possible penetration.
Let’s understand these 5 Mac security tips to ensure your Mac device is an impenetrable fortress of mobile data.
Use LoJack to Recover Data If Stolen
Do you travel with your MacBook? If yes, then you need to remain prepared for situations like theft of the device. You may also lose the MacBook due to your absentmindedness. As these devices contain lots of personal and professional information, losing them can cause serious privacy issues for you. So, you must make sure that you get the unit back as quickly as possible.
LoJack is software for MacBook that provides data security as well as a theft recovery. It assimilates at the level of BIOS firmware. As a result, it does make the device untraceable even after the removal of the hard drive. That’s the worst surprise for thieves! LoJack broadcasts the precise location of your device, without the thief knowing about it.
While this does not guarantee that your MacBook would be in its same condition, odds improve significantly. You can also consider Mac VPN to secure the system and add another security layer between the Internet and your Mac device. This helps you hide your current IP address and encrypt your online traffic in such a way that hackers and cybercriminals cannot see it. Further, this ensures added protection from censorship, interference as well as snooping online.
Enable MacBook macOSSecurity
Even when using a MacBook, you might become a victim of data theft. This happens primarily when the user forgets to enable macOS’s pre-installed security features. Disabling these features does no good to the device. Hence, users have to enable the security features to make sure their privacy is protected from cybercriminals. Some of the things you must secure are:
- Disable Auto-login Function and Set Password: While you may not want to enter the password time and again, you have to. It’s like keeping the front door to the house open. With a checkbox to click and a password, this feature is enabled. It works as a roadblock for hackers.
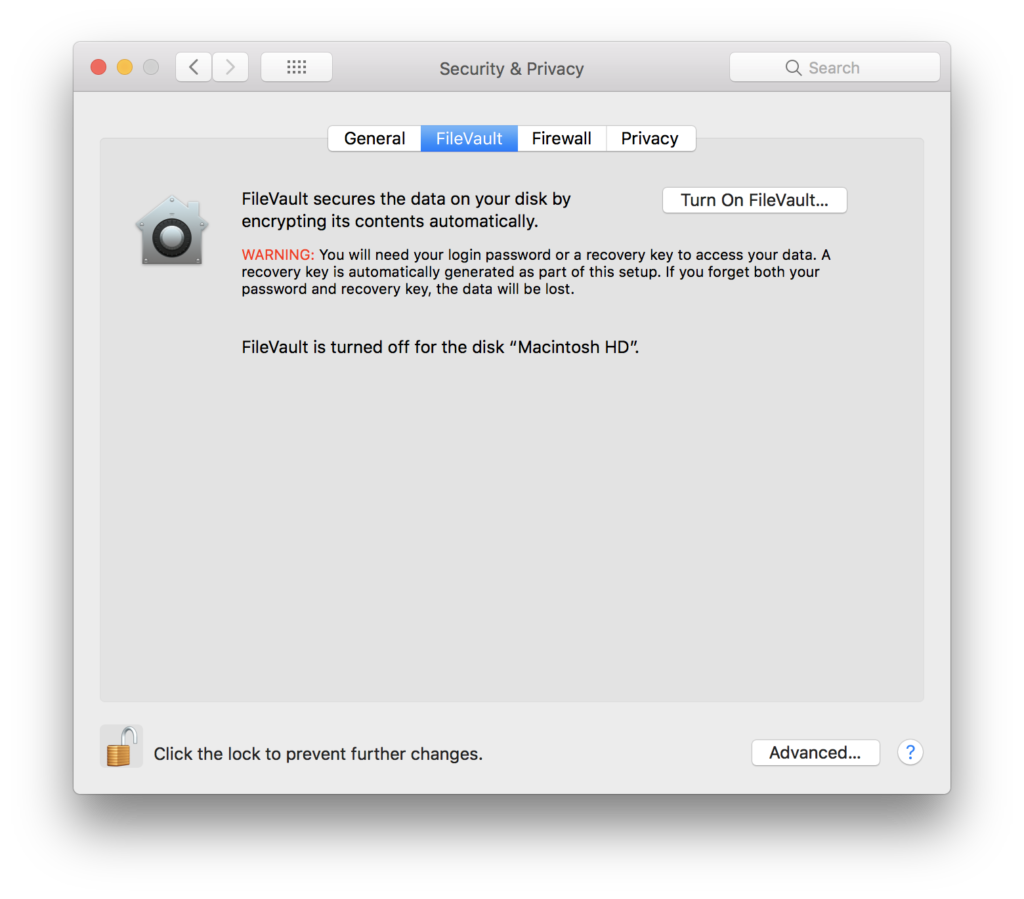
- Enable FileVault Encryption: If your MacBook is stolen and you believe that as you have a password, your data is safe, you are wrong. Most data thieves and hackers pull out the hard drive and install it in another device using IDE/SATA to the USB cable. The computer can read the drive of your MacBook just as another USB drive or DVD. To prevent this, you should enable file encryption with OSX’s FileVault. It encrypts as well as decrypts files related to the profile with a password.
- Turn-on Firewall: Mac has a built-in Firewall to thwart attempts of attackers to break into the device using the internet. Users can set up a firewall to block any malicious incoming network link and regulate the outgoing traffic.
Install Patches
To use your Mac devices to their full potential, you must protect them from hackers. Modern-day hackers are extremely prompt in detecting weaknesses in applications and quickly come up with methods of exploiting them. If you don’t keep your system protected from such unscrupulous people, you might end up becoming victims of identity theft, data theft, and loss of financial assets.
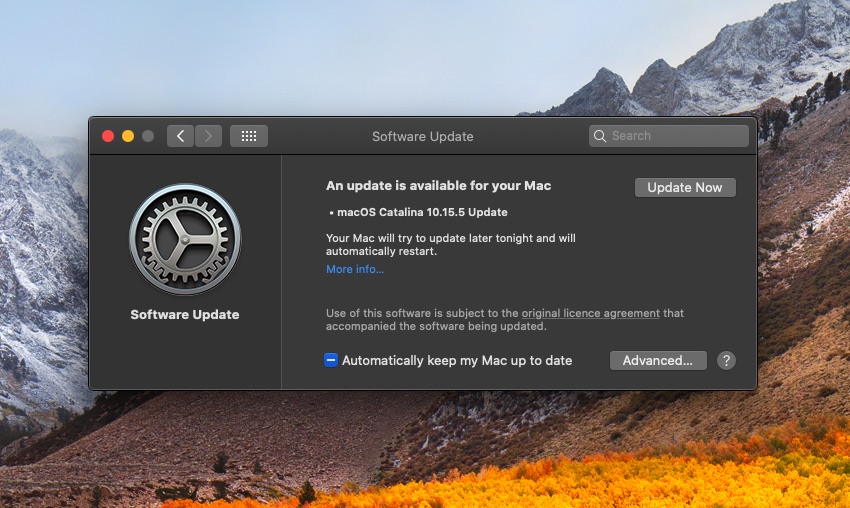
Developers address these vulnerabilities and prepare patches to fix the same. Users can install these patches to ensure smooth function.
macOS checks software updates regularly. It prompts the user to download an update and install it. Some third-party software like MS Office introduced their software update apps that regularly check for available patches. The remaining apps have a “Check for Updates” feature to be used manually.
It’s best to perform these checks weekly for the frequently used applications so that you are least vulnerable.
Lock
Indeed, it’s extremely difficult to fight thieves looking to steal a high-end device like the MacBook. However, if you don’t walk the extra mile to keep these dishonest individuals at bay, you will not only lose an expensive belonging but will also leave all your confidential data at risk of being stolen. Ideally, you must discourage them so much that they may leave the thought of targeting your MacBook.
There are many security devices available in the market that physically connects the MacBook with a robust loop of steel cable to something large, such as furniture. MacBook features Kensington Security Slot, or K-Slot, that accepts these types of locks.
Hard-shell Configuration Protects the Center of Mac
Even a minor lapse in the security of your MacBook might cause serious issues for you. You may end up exposing confidential information like your contact details, bank account number, business turnover, social security number, etc. to corrupt people.
If you are serious about the security of your MacBook and you would like to delve down deeper into the settings to ensure security, download and install the macOS security configuration guide. These put together the details of documents and settings available to lock down various aspects of Mac OS.
However, make sure the security of your MacBook strikes a balance with its usability. You should not lock the device so tightly that you fail to enter it.
Conclusion
To ensure data privacy and security, following the aforementioned steps is pivotal. Enabling macOS security or using LoJack, installing patches, downloading a Mac VPN, or locking your MacBook are all important hacks to keep in mind for keeping your Mac device safe from hackers. Additionally, the hard-shell configuration also helps to maintain confidentiality.