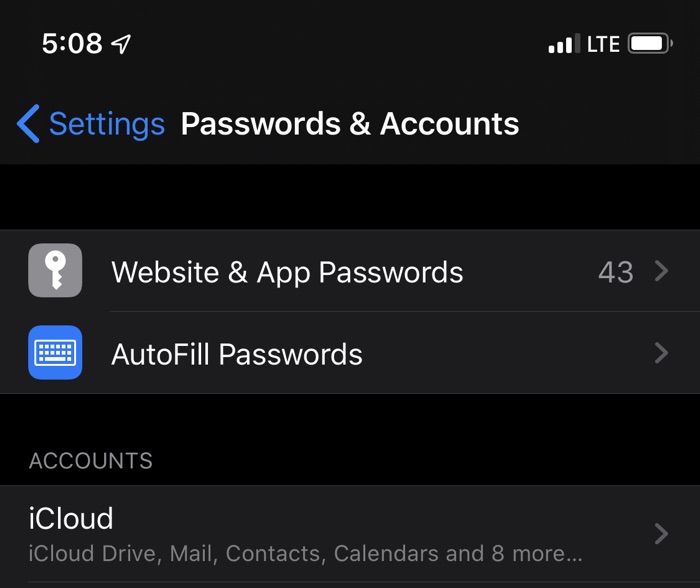
If you are running iOS 13 Developer beta on your device, then there’s a major bug that you should know about. This particular iOS 13 bug gives other people access to “Website & App Passwords” data through the Settings application by bypassing the Touch ID and Face ID authentication. The bug was found in iOS 13 developer beta 3 and iOS 13 Public beta 2. Both developer and public betas for iPadOS 13 are also affected by this vulnerability.
How the bug works is simple, in order to access usernames and passwords stored in iPhone’s iCloud Keychain anyone can access the Settings app and tap on ‘Website & App Passwords menu repeatedly while avoiding the prompt asking for Touch ID/Face ID authentication. User can continue to tap on the menu and after several tries iOS will eventually give access to stored login data and passwords without even authenticating first.
As iOS 13 is currently in beta, presence of such bugs isn’t a big deal. In fact it is a good news that the bug has been discovered and reported to Apple during the beta process as the company will now be able to fix it before iOS 13 is released to public.
It is better to be safe than sorry
It is important for beta testers to know about this bug’s existence in case they hand over their devices to other people in unlocked state, something people often do when showing off new iOS features. You can stay safe from this vulnerability by not handing over your iPhone or iPad to someone. To take advantage of this iOS 13 bug the device needs to be unlocked or the attacker needs to know the passcode of your device. The easiest way you can stay safe is by not handing over your iOS 13 powered device to someone until Apple has fixed this issue in the next beta release.
Apple is currently beta testing iOS 13 and iPadOS 13 with developers and public. Currently we are expecting the fourth developer beta and third public beta to be released soon, and we are hoping that this particular vulnerability will be fixed in the upcoming release.